Hide My WP Ghost Lifetime Deal: WordPress Security Plugin

Hide My WP Ghost is a highly configurable WordPress plugin that makes it simple to upgrade your site’s security in a matter of minutes and to better defend your site. You’ll be able to stop hacker bots in their tracks and prevent them from compromising data such as plugins, themes, and the core files of your WordPress installation.
This tool scans your entire site to determine its current security level and to identify urgent security threats that leave your site vulnerable to a variety of different types of cyberattacks. Protect your website against common attacks such as script and SQL injection, as well as brute-force attacks, by masking the vulnerabilities that are exposed without changing any files or directories on your server.
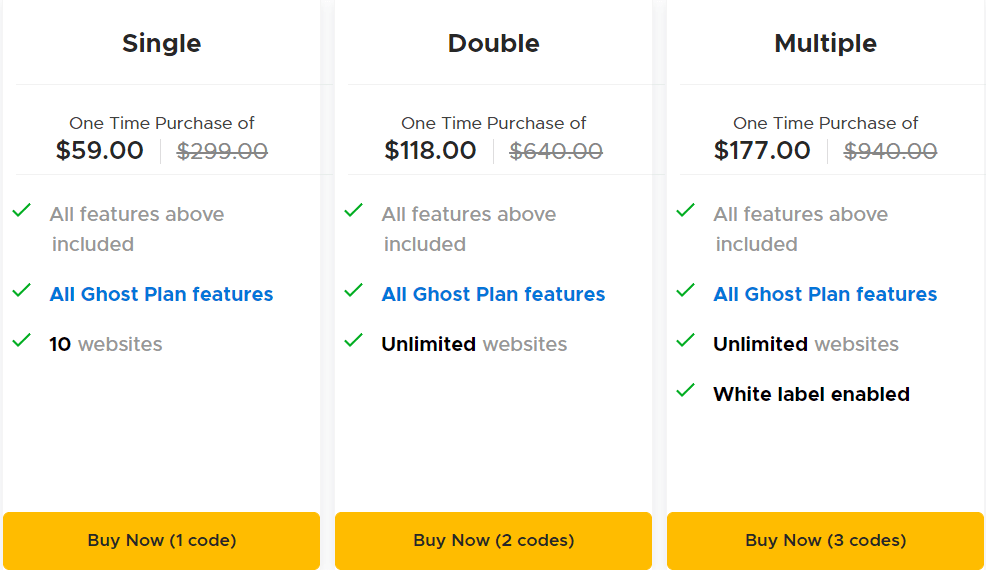
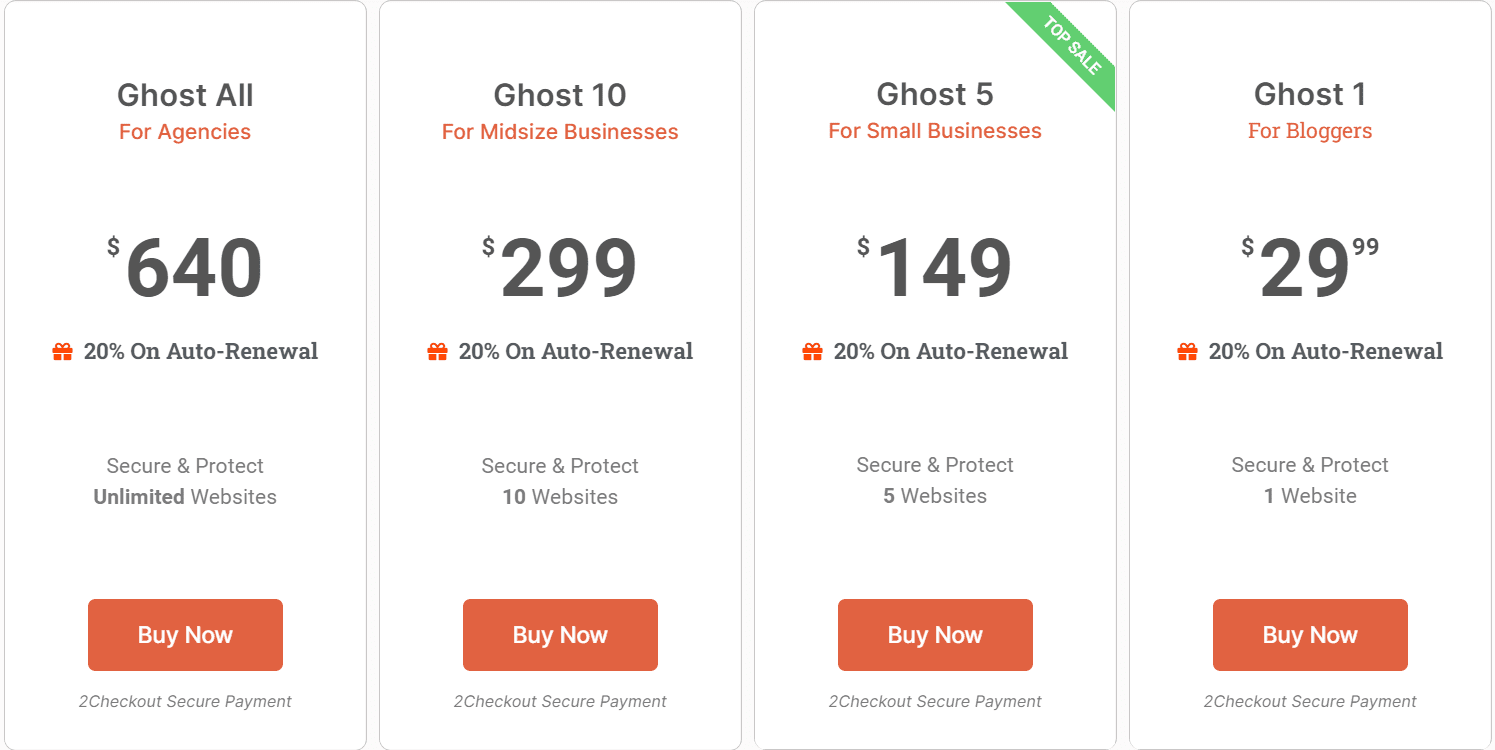
Hide My WP Ghost Lifetime Deal Features Overview:
Never miss a deal again! Get Subscriber Exclusive deals and discounts weekly
Lifetime deals on Software, SAAS and apps for small business and Entreprenuers. Updated daily with the latest deals from all over the internet.
Leave a Reply